Azure AppSec Starter Guide
The Urgency of Application Security in the Cloud
Table of Contents
- Understanding Application Security in the Cloud
- A Framework for Continuous Protection
- Why It Matters More Than Ever
- Busting Some Common Myths
- Real Incidents That Make the Case
- Strengthening Your Cloud Security Posture
- Final Thoughts
Understanding Application Security in the Cloud
In today’s cloud-native landscape, migrating applications to the cloud offers agility and scalability—but it also introduces evolving security challenges. A common misconception is that the cloud provider handles all aspects of security. In reality, security in the cloud follows a shared responsibility model: while the cloud provider secures the underlying infrastructure, customers are responsible for securing their applications, data, and access controls.
Application security in the cloud involves a continuous process of identifying vulnerabilities, patching weaknesses, and preventing future threats—especially under the shared responsibility model.
A Framework for Continuous Protection
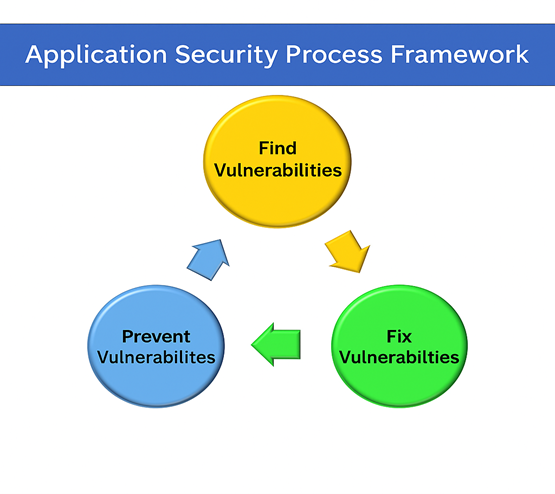
A simple three-step cycle can help you embed security into every stage of the app lifecycle:
1. Find Vulnerabilities
Catch issues early with automated tools:
- Static & Dynamic Analysis (SAST, DAST)
- Software Composition Analysis (SCA)
- Microsoft Defender for App Services
- GitHub Advanced Security
2. Fix What You Find
Remediate issues before they become incidents:
- Apply secure coding best practices
- Patch third-party dependencies
- Integrate fixes into CI/CD pipelines with Azure DevOps or GitHub actions
3. Prevent Future Issues
Harden your systems to avoid repeat flaws:
- Adopt shift-left security practices
- Enforce Azure Policies
- Educate developers and automate security guardrails
Why It Matters More Than Ever
Threat actors are faster, smarter, and more resourceful today. Here’s why you need to stay ahead:
- More Public-Facing Apps: Increased exposure to external threats
- Open-Source Integration: Hidden vulnerabilities in third-party libraries
- Gaps in Developer Awareness: Security is often overlooked during development
- Flexible Configurations: Can lead to misconfigurations and insecure defaults
- Unencrypted Communication: Risks data leakage in transit
- AI-Powered Attacks: Advanced tools make exploitation easier
Busting Some Common Myths
It’s easy to think you’re safe with:
- Antivirus software
- SSL/TLS encrypted traffic
- Firewalls and VPNs
While helpful, these tools focus on network and infrastructure, not on your application’s logic and codebase, which is where vulnerabilities like XSS and SQL Injection live.
Real Incidents That Make the Case
SQL Injection – Freepik & Flaticon Breach
Hackers exploited an SQL injection vulnerability in the Flaticon website to steal emails and password hashes of 8.3 million users.
🔗 Read MoreCross-Site Scripting – Fortnite
A stored XSS flaw in Fortnite’s old website allowed attackers to hijack accounts and make purchases using users’ saved credit card details.
🔗 Read MoreDDoS Attack – Dyn DNS Outage
A massive DDoS attack on Dyn disrupted internet access to major platforms including Twitter, Netflix, and GitHub.
🔗 Read MoreAPI Exposure – Twitter API Vulnerability
A flawed API allowed attackers to match phone numbers with Twitter usernames, exposing sensitive information.
🔗 Read More
Strengthening Your Cloud Security Posture
To build secure, cloud-native applications, consider a Zero Trust approach—never trust, always verify.
Key Strategies from Azure cloud
- Azure Front Door + WAF: Stops threats at the edge
- DDoS Protection: Mitigates large-scale denial of service attacks
- Virtual Network Isolation: Separates workloads using VNets and NSGs
- Azure Firewall: Centralized traffic control with stateful rules
- Application Gateway with WAF: Protects Layer 7 HTTP apps against OWASP Top 10
- NSG, ASG, and UDRs: Fine-tuned traffic segmentation and control
- Service Endpoints: Restrict access to Azure PaaS services like SQL and Storage
- Private Endpoints: Enable secure, private IP-based access to Azure PaaS services like SQL, Storage, and Web Apps.
Final Thoughts
Security can’t be bolted on—it needs to be built-in. In the cloud, where change is constant and threats evolve rapidly, application security is not just important—it’s urgent.
Whether you’re developing the next big SaaS platform or modernizing legacy systems, investing in secure application architecture is critical. The earlier you embed security, the stronger and more resilient your cloud journey will be.
Further Readings & References
Overview of Defender for App Service
Protect your Azure App Service web apps and APIs.
🔗 Read moreSecure Development Best Practices
Guidance on building secure applications in Azure.
🔗 Read moreSAST & DAST Tools (Free for Open Source)
A list of free Static and Dynamic Application Security Testing tools provided by OWASP.
🔗 View tools
Want to learn more or discuss cloud security best practices? Connect with me on LinkedIn.
This blog linensed to TechAdvantX Inc